Hello All. So unless you have been hiding under a rock somewhere, you probably have heard about about the SolarWinds breach and further compromise of the integrity of their software and update facility.
I am not going to get to far into the backstory of the breach as their have been so many deep dive explanations of this including some great posts on the mechanics of the malware:
I will however provide a VERY brief and quick synopsis:
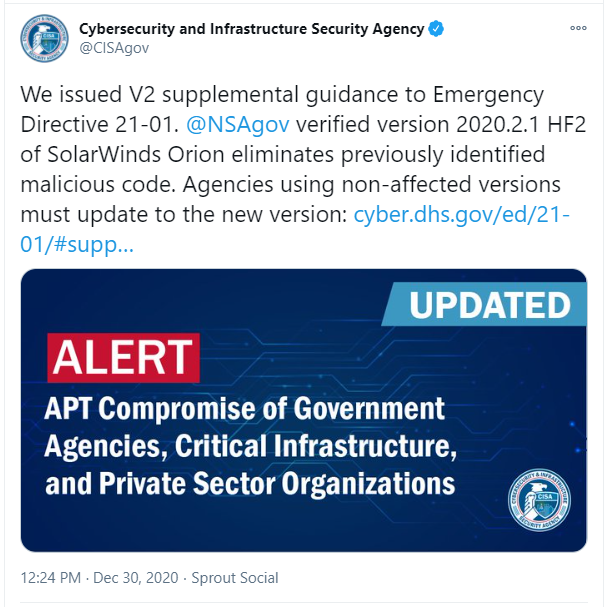
- SolarWinds Orion Supply chain Attack – AKA SUNBURST or Solorigate perpetrated most probably by a Russian government sponsored group known as UNC2452 (FireEye), Dark Halo (Volexity), SolarStorm (Palo Alto) or APT29/Cozy Bear.
- 18,000 initial customers have the malicious update installed (this may not necessarily mean all of those organizations have actually been breached).
- A patch (hotfix) was made available by SolarWinds on December 15.
- The malicious binaries are detected and removed by Microsoft Defender since December 16.
- The main C2 infrastructure domain has been seized and sinkholed by Microsoft and the security industry and is now being used as a Killswitch for the malware.
- In addition to the SolarWinds flaw, there may have been additional initial access vectors. This is still being investigated.
- Palo Alto identified a second backdoor used in some cases, which may indicate a second attacker.
- From SolarWinds’ own advisory, which was last updated on 24 December: SolarWinds Orion Platform software builds for versions 2019.4 HF 5, 2020.2 with no hotfix installed, and 2020.2 HF 1 are vulnerable. Log into the SolarWinds customer portal to download hotfix release 2020.2.1 HF 2.
Also a great diagram from Microsoft describing the attack:
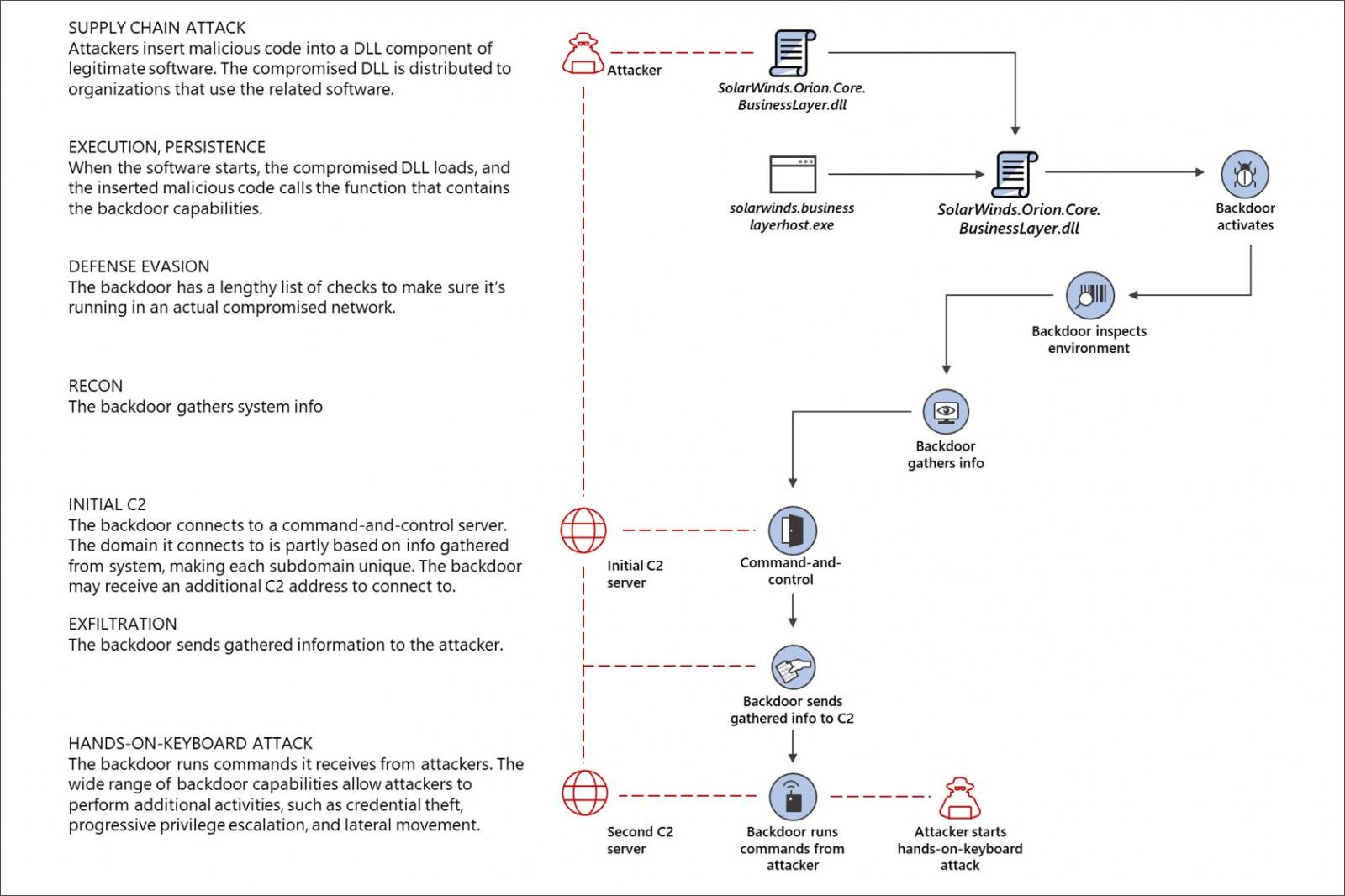
So what is the fallout thus far? Is this survivable for SolarWinds?
A number of very large fortune companies as well as governments have been affected including Cisco, Intel, Deloitte, Nvidia, VMware as well as many governments including that of the US. This was such a big breach that it triggered a Whitehouse National Security Council meeting on Dec 13. Now other companies have survived these types of breaches in the past. Not nearly as notable, but companies like Zoom has seen their share of issues and most recently FireEye, an infosec company known for assisting organizations with nation state breaches (Mandiant) was breached by a nation state. Both are still going strong. So I guess time will tell. Much like Zoom’s purchase of Keybase to show how critical security was to the company, SolarWinds (although they have security products), should take a break from product company acquisitions and make a strategic buy of a known company in the security space to improve its security and as a byproduct improve its image.
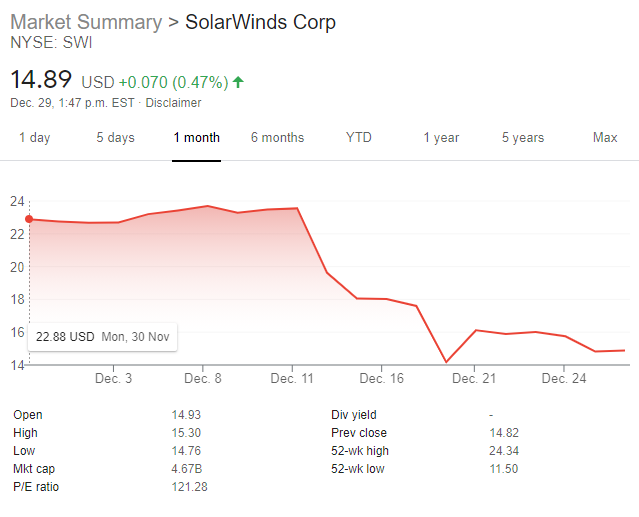
I mean their stock has certainly taken a beating, selling for $22.88 USD on Nov 30 and now selling for $14.89 USD. It looks like the stock has flatlined, however, we are in the middle of a holiday stretch. The interesting details related to the stock is the dramatic drop on Dec 11 which coincides with the public announcement of the breach following breach investigation where FireEye discovers that SolarWinds Orion updates had been corrupted and weaponized by hackers. Now the interesting bit is on Wednesday, December 9, 2020 a CEO transition plan and stock transactions were announced – two days before SolarWinds apparently knew about the breach. This includes:
- SolarWinds CEO Transition: The company discloses Sudhakar Ramakrishna will succeed Kevin Thompson as SolarWinds president and CEO, effective January 4, 2021. The CEO announcement is made before FireEye apparently alerts SolarWinds about the breach two days later on December 11.
- SolarWinds Stock Transactions: On the financial front, Canada Pension Plan Investment Board (CPP Investments) has made a $315 million secondary investment in SolarWinds. The deal involves CPP buying an existing stake from private equity firms Silver Lake and Thoma Bravo, and their respective co-investors. The transaction disclosure is made before FireEye apparently alerts SolarWinds about the breach two days later on December 11.
Furthermore, SolarWinds investors traded $280 million in stock days before hack was revealed. Don’t forget another important tidbit in the timeline – on Dec 8, FireEye discloses that state-sponsored hackers broke into FireEye’s network and stole the company’s Red Team penetration testing tools – same people that were investigating the breach at SolarWinds…thankfully the breach on FireEye, identified the malicious lines of code in Orion. I assume the SEC is already knee-deep in investigating this.