Hello All. So WordPress can be a great CMS platform and allows you to put a pretty nice site up fairly quickly. Most recently I was working on a WordPress breach and wanted to take the opportunity to remind folks about some of the controls they should put in place to avoid having any security-related issues. Hopefully everyone finds this information useful. Please drop me a line if you think I should add anything to this list.
WordPress Core Updates
It goes without saying that you should keep this up to date. Much like updating Windows, when updates come out, be sure to get them installed. WordPress development team are pretty diligent at getting updates out as soon as possible when a vulnerability is identified. At the time of this post, version 5.6.1 is the current version (released on Feb 3, 2021) – it was a maintenance release for the 5.6 branch. Please see the following for release notes and an idea of the frequency of updates – http://bit.ly/3aChahk and http://bit.ly/3jhIB44
Two-Factor Authentication
If you run a WP site today, you will know from your logs that there are automated bots from all over that try to brute force there way into your WP admin page. I recommend installing a two-factor authentication plugin. There are many, and for the most part are free. Check out Duo which allow up to 10 free users, or Google Authenticator..
Logging
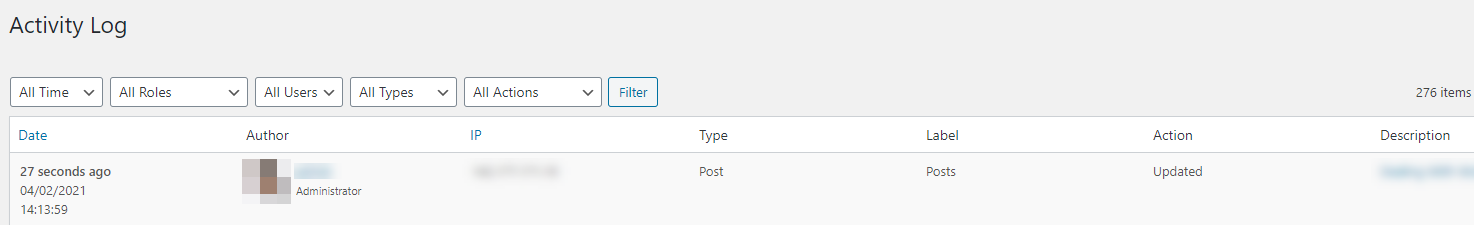
So if you are new to WP, I would recommend installing a site security plugin to ensure that you can track when people log in, when changes occur to your site, etc. This is key so that if something occurs on your site, you will receive an email to notify you. A couple of good plugins are Sucuri Security, WP Security as well as a tool called Activity Log. There are more, but these are the ones I have seen to work well. Here are a few screenshots:
Activity Log will provide a log of any changes to the site including date/time, who made the change, source IP, the type of change (i.e. Post) and the page that was updated.
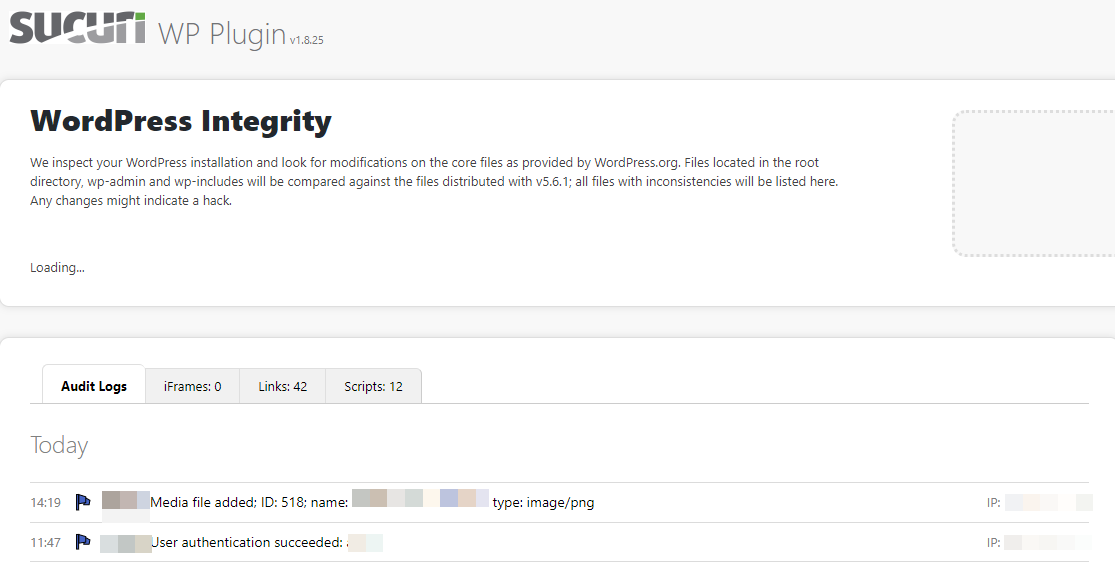
Sucuri is another really good tool. It does all kinds of things from a security perspective, but from a logging perspective, it is very similar to Activity Log:
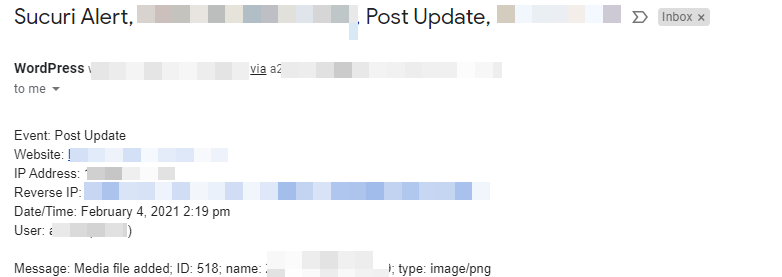
It also has the option of sending emails such as this when activity occurs:
Plugin Security
This is a VERY key component and what typically gets people in a lot of trouble. Installing whatever plugin the see and not thinking about the outcome. You have to understand, some of these plugins are pretty benign, but a number of them need write access at times to the file system, etc. This can be very dangerous. My rules of thumb when it comes to plugins are:
- KISS – keep it simple stupid – only install the bear minimum number of plugins. Be smart here, if you don’t need it, don’t install it.
- Review your plugin install base regularly – if you no longer need it, get rid of it.
- Where did your plugin come from – you want to check a few things. First, I don’t normally trust plugins that are not on the WordPress.org site. If they haven’t made it there, I would be suspicious. Now, that is not to say that all plugins on the WordPress site are safe, but it is a start.
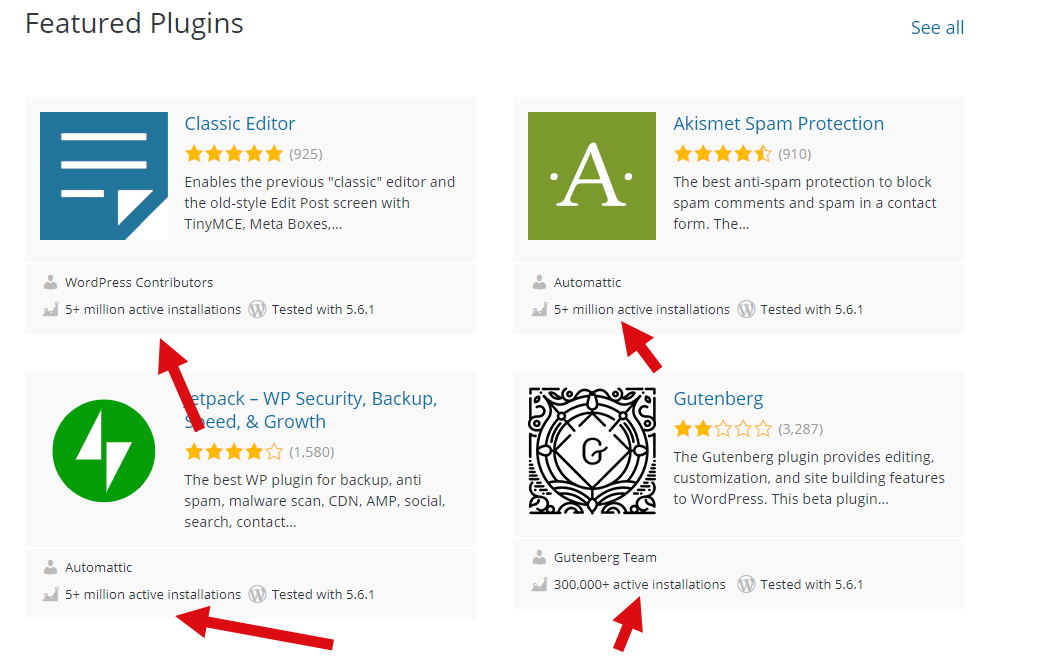
- What is the install base of the plugin – typical mainstream plugins have 500k+, 1M+ installs. Anything in the 20k or below, well, try and find an alternative. This means the plugin may be relatively new and could have a number of unidentified vulnerabilities.
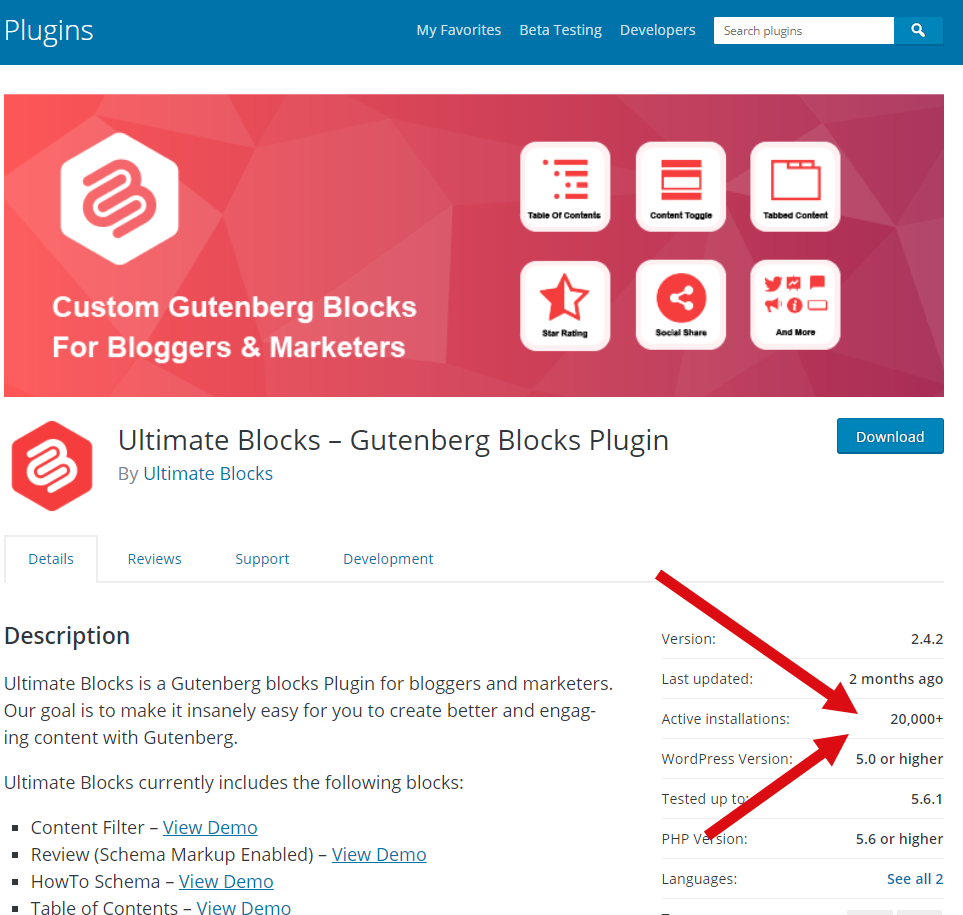
vs.
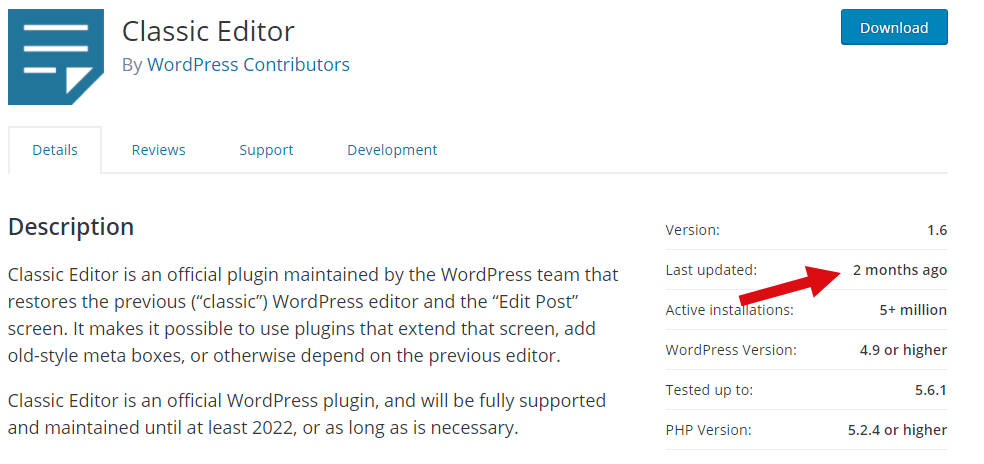
- Last update – another important thing to look at is how often the plugin is being updated and what version of WordPress is supported. This could mean the plugin has gone stale and no one is actively supporting it. Very bad if a vulnerability is identified. The WordPress site will actually warn you when it has been a long time since the plugin was updated.
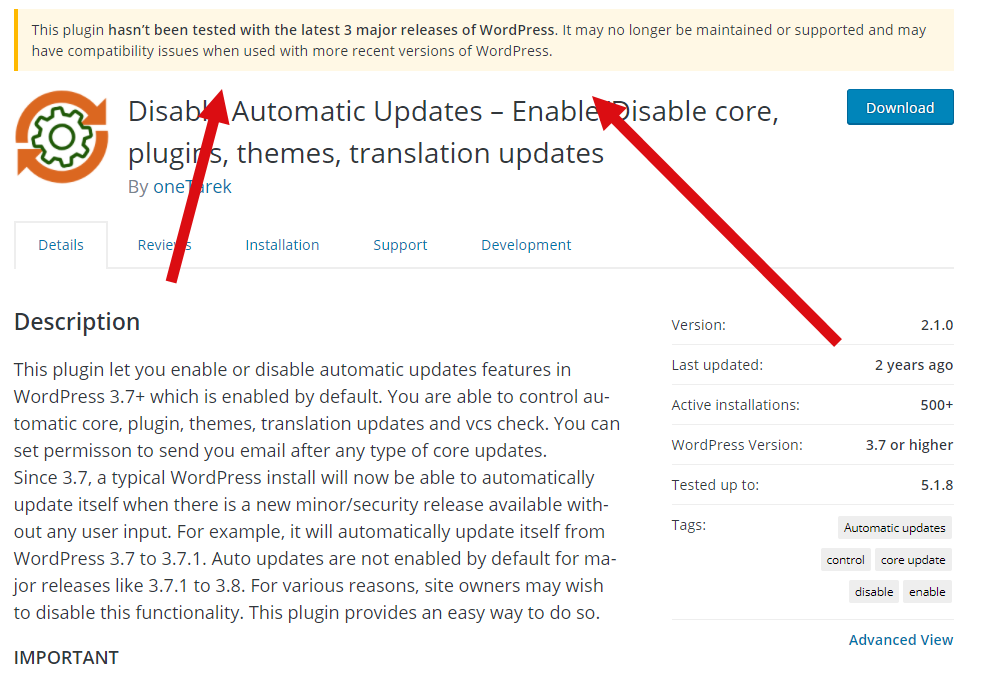
- Did it make the “bad” list – ok, this isn’t at the bottom of the list because it is the least important. Trust me, this one is equally important if not more important. Make sure you do a bit of research on the plugin before installing. Sites such as WPScan WordPress Vulnerability Database catalog over 20k known plugin, theme and core WP vulnerabilities. The site gives you a wealth of information. And who knows, maybe they’ve fixed that plugin you want to use.
- Back it up – Before you install any plugin, make sure you back up your site. There are many plugins and methods you can use to easily backup your site. Given you don’t necessarily know what the plugin is doing when you install it, backups are key.
Final thoughts on plugins – When in doubt, don’t use it. I also tend to look at things like the rating and comments left by people on the WordPress site, whether their is support for the plugin, etc.
Reverse Proxy / Cloud Proxy
Another good idea would be to look into a reverse or cloud proxy. Essentially what happens here is a server or cloud service is placed in front of your WordPress site and the traffic can be screened prior to hitting your site. You can do geo-blocking from here, block certain common attack attempts (i.e. login brute-force) and many of the cloud services also block based on intelligence (i.e. known bad plugins, etc.).
If you are running your own server, you can stand up an Apache server running the mod_security module. Here is a good site on how to do that – http://bit.ly/2Lp2WYU and more details on mod_security and WordPress – http://bit.ly/2YLSrle.
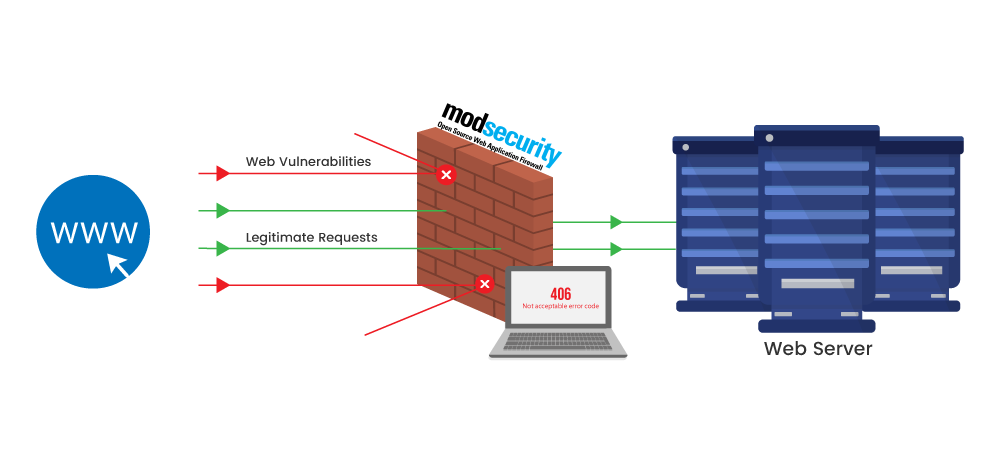
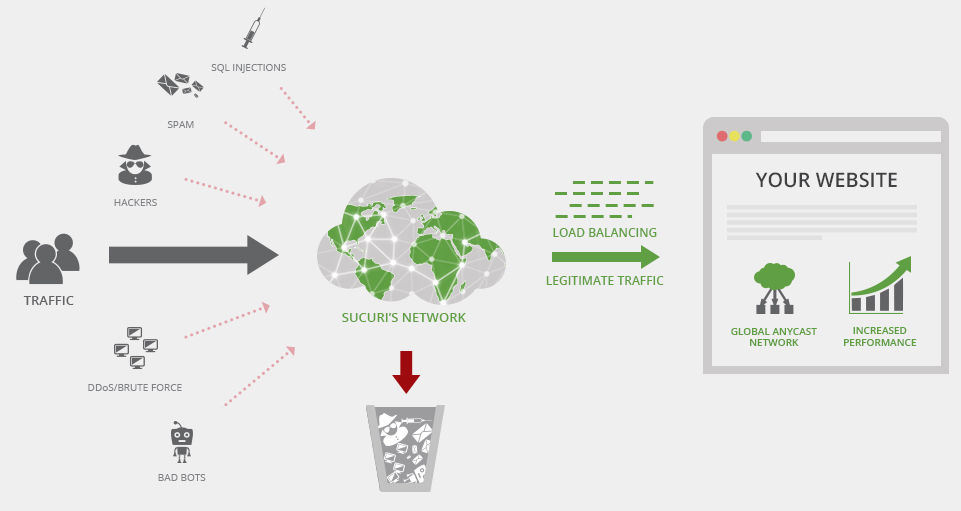
Now if you can afford the $9.99 / month, I would highly recommend looking into Sucuri’s Web Application Firewall. These guys are WordPress experts and their cloud-based proxy works very well.
Backups
I highly recommend you ensure you have regular backups of both the WP database as well as the WP files (i.e. plugins, core, themes, etc.). You never know when something will happen and having a good safe backup to restore to can be a lifesaver. Sucuri have a good service, as well as VaultPress. If you want to do it on the cheap, a simply tarball of the files and a mysqldump of the database will do.
Encryption
In this day and age, SSL is considered normal best practice. I would recommend installing SSL at a minimum to protect you while you are in the admin console of WP, although it doesn’t hurt to just push everything to SSL. There are a number of plugins out there to facilitate this (i.e. Really Simple SSL). SSL certs are fairly cheap, but if you want to go the free route, services like Let’s Encrypt will work, however, be aware their certs need to be renewed normally every 90 days. There are lot’s of sites out there that explain how to install these – here is an example.
Final Words
There are a bunch of other items I didn’t include in this post – given I could probably write a book about this. You still need to ensure your underlying infrastructure is sound, the version of PHP installed is safe, you aren’t exposing services on the server or your cloud host is reputable and safe. Here is another good source for WP security – https://www.wpbeginner.com/wordpress-security/
![]()
![]()
![]()


![]()