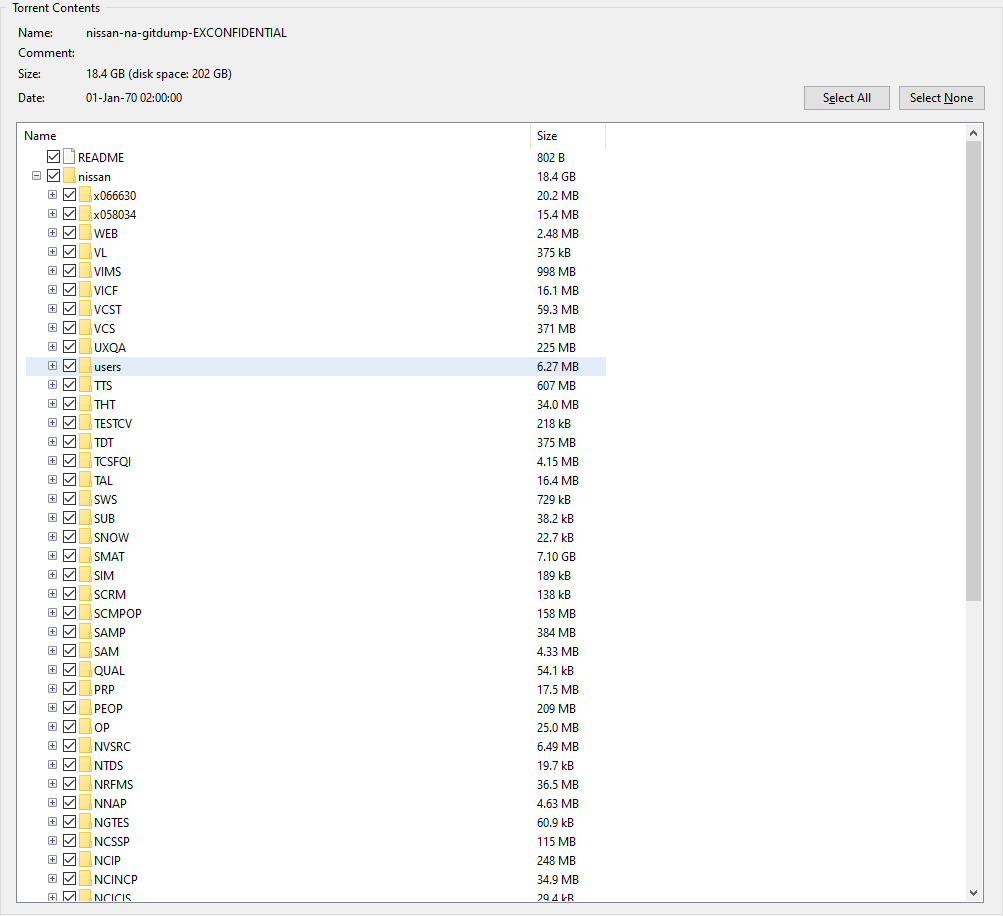
Hello All. US President-Elect Joe Biden has confirmed that cybersecurity is a priority for the incoming administration with the addition of Anne Neuberger, the NSA’s Director of Cybersecurity as its the new Whitehouse Cybersecurity Coordinator and member of the National Security Council (NSC).

Given the recent SolarWinds breach and the steady increase or foreign cyberattacks from nation states such as Russia and China, I think Biden, or at least his advisors understand that this is an important seat at the NSC table. For those of you who may not remember, it was in 2018 when then National Security Advisor, John Bolton eliminated the role filled by Rob Joyce, former Tailored Access Operations unit with the NSA. Bolton said the post was no longer considered necessary because lower-level officials had already made cybersecurity issues a “core function” of the president’s national security team. Most of us in the industry were baffled by this move.
I know about the importance of the role well enough having heard numerous stories from my good friend, the late Howard Schmidt who served as the inaugural WH cybersecurity coordinator for President George W. Bush and returned to the role under President Barak Obama. He mentioned how critical the role was in advising the President via the NSC.
The new appointee, Anne Neuberger, joined the NSA more than a decade ago and has been serving as the agency’s director of cybersecurity since 2019, will be named deputy national security adviser for cybersecurity in the incoming NSC. She will be responsible for coordinating the fed’s cybersecurity efforts. She will most probably focus on responding to the attacks campaign by Russian hackers in 2020. She is a perfect candidate for the role. She was the NSA’s first director of cybersecurity, responsible for managing intelligence information sharing between the NSA and other government agencies, as well as the private sector, about threats to country’s critical infrastructure.